When a dynamic object expires, it is completely deleted and does not go through the AD recycle bin. It is also not visible in replication metadata.
Monitoring creation events is important to ensure that these objects are not used for malicious activities.
First of all, you need to configure auditing (SACL) on the domain and advanced logs for Directory Service Changes. You can follow the Netwrix documentation.
Next, create a filter using the XPATH query to filter all events relating to the creation of dynamic objects (OID 1.3.6.1.4.1.1466.101.119.2 = dynamicObject). For the example, my view is called DynamicObjectCreation.
<QueryList>
<Query Id="0" Path="Security">
<Select Path="Security">*[System[EventID=5136]] and *[EventData[Data[@Name='AttributeValue']='1.3.6.1.4.1.1466.101.119.2']]</Select>
</Query>
</QueryList>Your filtered view now contains all dynamic object creation events:
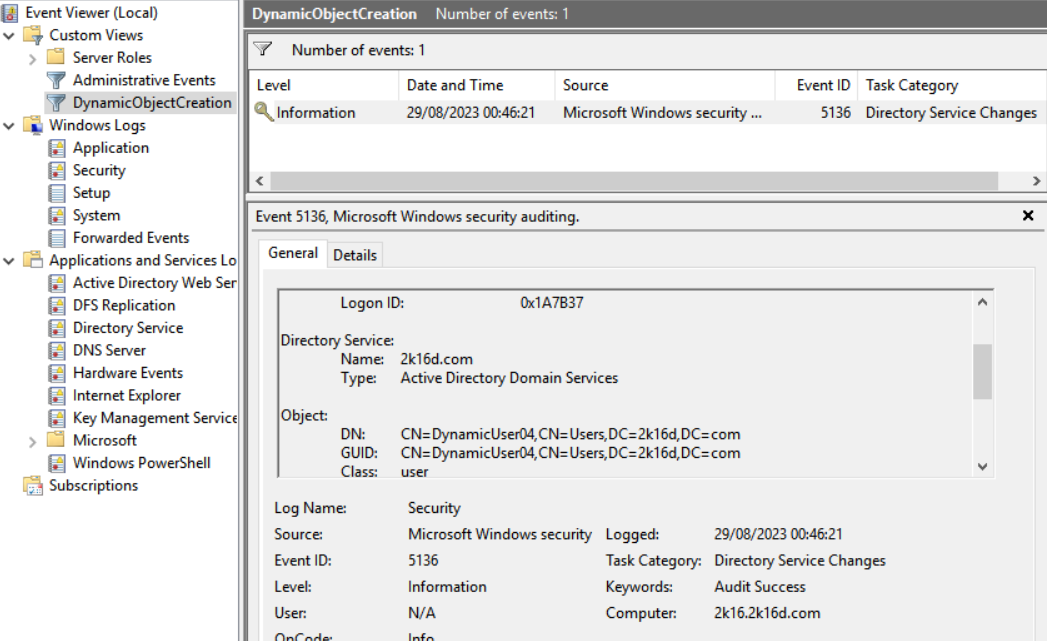
You can also use PowerShell :
$xpathFilter = "*[System[EventID=5136]] and *[EventData[Data[@Name='AttributeValue']='1.3.6.1.4.1.1466.101.119.2']]"
Get-WinEvent -LogName Security -FilterXPath $xpathFilter


Comments