In SAML (Security Assertion Markup Language), certificate-based signing is important for ensuring the integrity and authenticity of SAML messages.
When a SAML message is digitally signed using a certificate, it provides assurance that the message was not tampered with during transmission and that the sender of the message is who they claim to be.
It is important to get notified about token signing certificate expiration in SAML because if the certificate used for signing SAML tokens expires, it can cause disruptions to the SAML-based authentication and authorization process.
Azure AD provides the ability to configure notification addresses to receive alerts on certificate expirations. Notification Email to receive alerts about certificate expirations. You can configure it Your app > Single Sign-On > SAML Certificates > Notification Email.
You can add several e-mail addresses. As the address can be internally or external, there is no verification about the e-mail address(es). So be careful to enter a valid e-mail address. Keep in mind a SAML signing certificate can be valid up to 3 years, so the notification email address must always exist in 3 years.
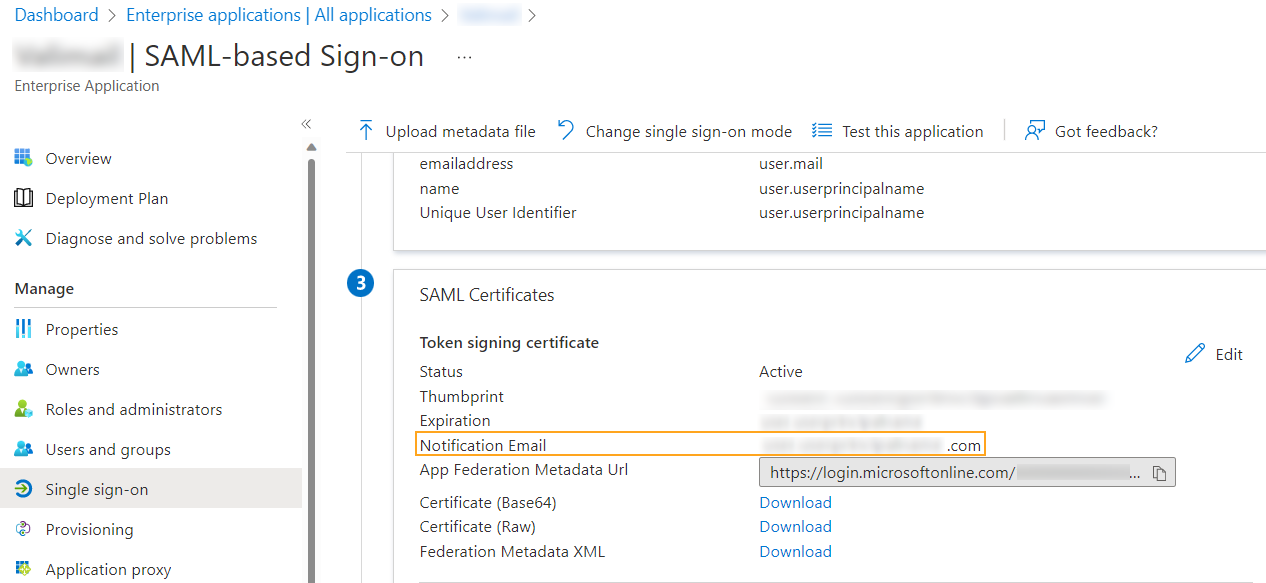
The notification email address in the SAML configuration is pre-populated with the user who configured the SAML settings. This can be problematic because the account used is often an administrator account that does not have a mailbox associated with it.
The following PowerShell code can be used to obtain important information about SAML-based applications, such as the certificate, the email address used for notifications and if the certificat is still valid.
Find the last version on my Github:


Comments