Error creating gMSA account in Entra Cloud Sync
When installing Entra Cloud Sync with a gMSA, you may encounter the following error:
Error while creating group managed service account (gMSA). Error: Unable to install service account pGMSA_xxxxxxxx$ after 6 retries

You can check the logs for more details in %ProgramData%\Microsoft\Azure AD Connect Provisioning Agent\Trace
There can be several causes for this issue. For this article, I will limit it to the one I encountered. The log content is as follows:
[07:22:47.786] [ 12] [ERROR] Exception caught while creating gmsa. Exception: System.InvalidOperationException: Unable to install service account pGMSA_xxxxxxxx$ after 6 retries
at Microsoft.Online.Deployment.Framework.Providers.GroupManagedServiceAccountProvider.InstallServiceAccount(String samAccountName)
at Microsoft.ActiveDirectory.SynchronizationAgent.Setup.Utility.ServiceAccountUtility.CreateGMSA(String domainFQDN, String username, String password, String& samAccountName, String& error)
[07:22:47.786] [ 12] [ERROR] Failed to create gmsa. Error: Error while creating group managed service account (gMSA). Error: Unable to install service account pGMSA_xxxxxxxx$ after 6 retries. KDSValidated: True.
Default account behavior
To fully understand the issue, it is important to know how the provAgentgMSA account is created.
In a default domain, the provAgentgMSA account is created in CN=Managed Service Accounts with the attribute msDS-SupportedEncryptionTypes set to 0x1C (28 in decimal), which allows the use of:
RC4_HMAC_MD5AES128_CTS_HMAC_SHA1_96AES256_CTS_HMAC_SHA1_96
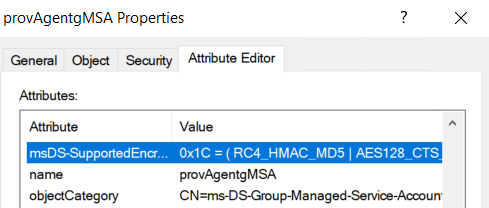
In my case, the issue comes from a domain-level GPO that enforces a minimum of 128-bit AES for Kerberos. As a result, my service account is created, but the msDS-SupportedEncryptionTypes field remains set as before, which causes a problem.
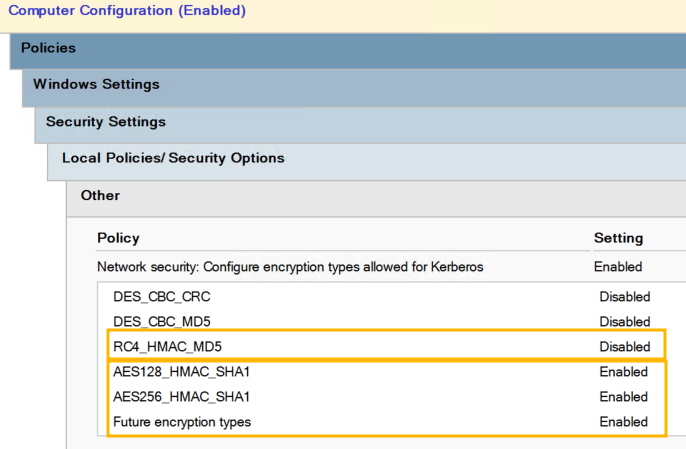
Fix
To resolve this issue, do not close the Entra Connect window. From a server with the PowerShell AD module installed and using an account with the required permissions, run the following command:
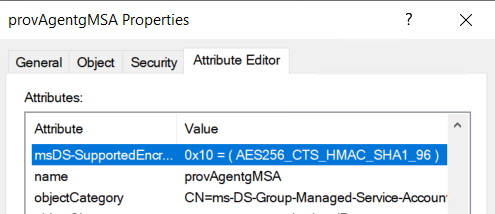
Get-ADServiceAccount -Filter "Name -eq 'provAgentgMSA'" | Set-ADServiceAccount -KerberosEncryptionType AES256The name pGMS_xxxx$ varies depending on the environment. The above command retrieves the gMSA account whose name remains the same regardless of the provisioning agent version. However, be careful if you already have another service account with this name (unlikely, but worth checking to avoid modifying the wrong account 😉).
Note that I specified AES256, but in my case AES128 would have been sufficient. However, I prefer to opt for the highest possible level.
Then simply click Confirm again in the Entra Connect Cloud Sync wizard, and the configuration will restart and complete successfully.



Comments