New Setting Users Can Create Azure AD Tenants (updated 2024 new graph module)
Published on 20 Nov 2022Clap
New setting means more control
In november 2022 (I haven't the exact date but it seems since 18th november 2022), many folks warned on a new setting in Azure AD: "Users can create Azure AD tenants".
What? Microsoft created a new security hole? 😱
This setting is not new. Since the beginning of Azure portal, every user can create Azure AD tenant with his corporate account. Until today it was a big problem because admins had no setting to prevent it.
With this new setting, the administrator now has better control over this. As shown below in the end user experience, the tenant created by user is not linked in any ways to the corporate tenant.
A Principal Product Manager from Microsoft (Jef Kazimer - @Jefftek on Twitter) confirmed this.
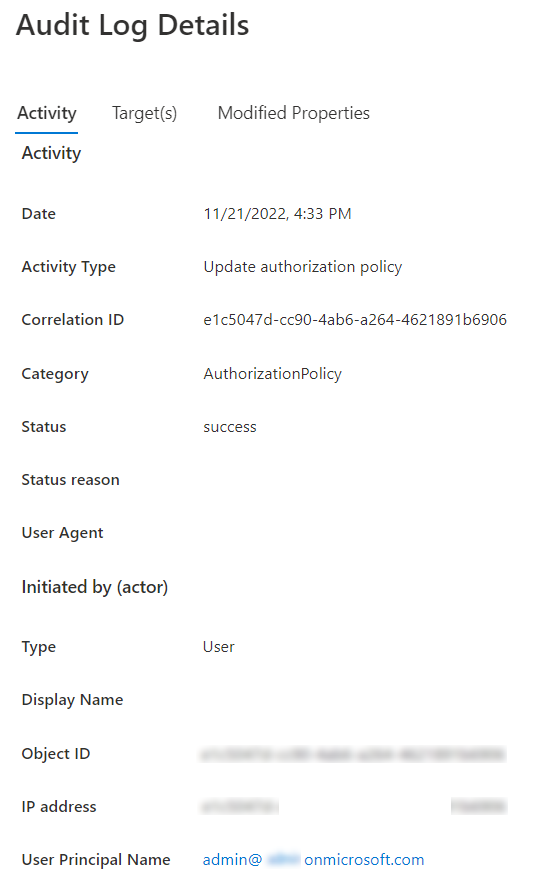
The ability to create tenants by users has existed in the Azure Portal since the beginning, Admins can review the tenant creation activity by users in the Audit logs. This new setting will allow admins to stop this activity entirely.
— Jef Kazimer (@JefTek) November 17, 2022
End user experience when creating Azure AD
There are several ways for a user to create an Azure AD tenant.
A simple google search for 'Azure AD tenant creation' leads to https://learn.microsoft.com/en-us/azure/active-directory/develop/quickstart-create-new-tenant. This article contains a direct link to Azure AD tenant creation: https://portal.azure.com/#create/Microsoft.AzureActiveDirectory
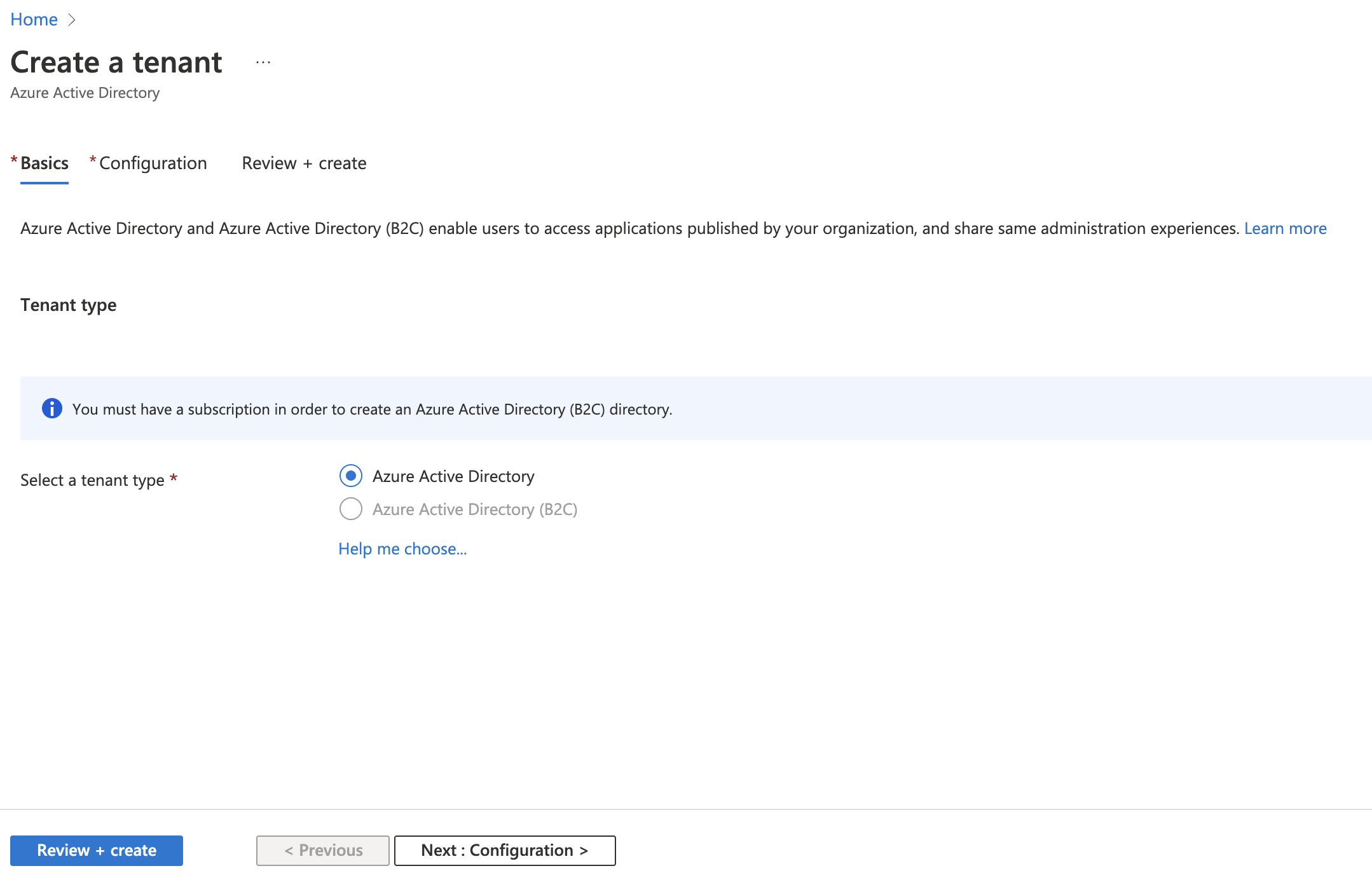
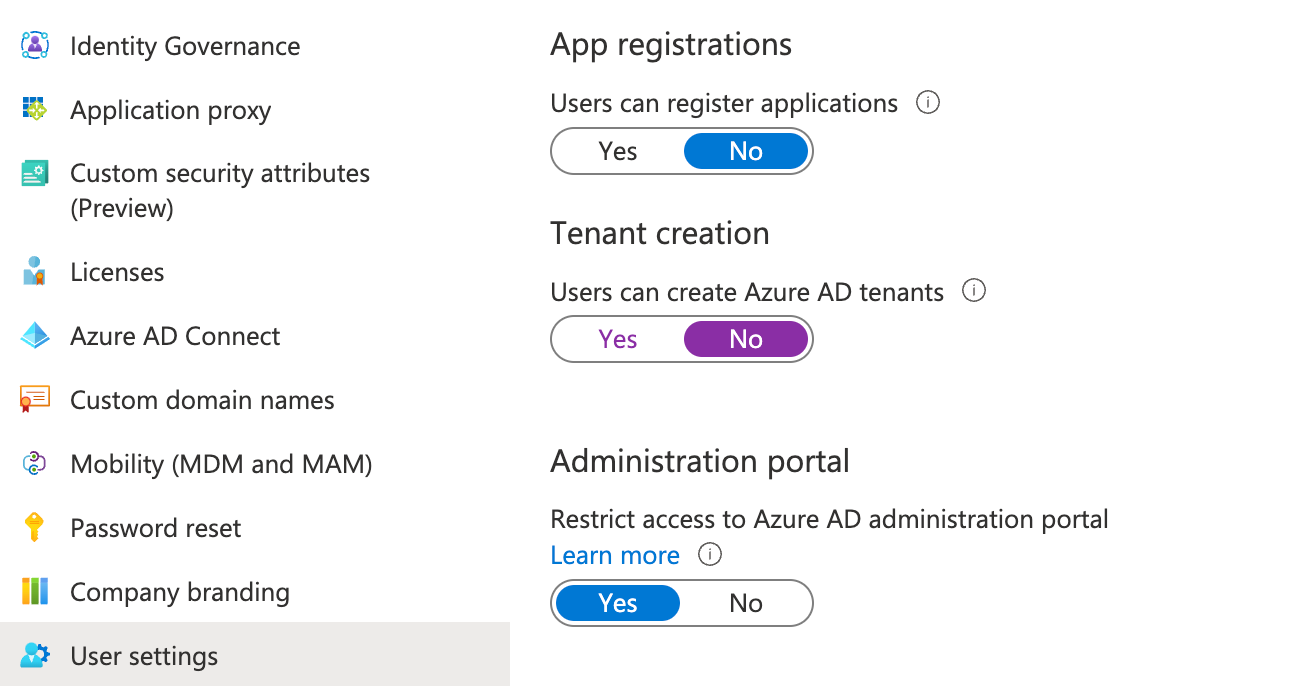
When an user goes to the Azure AD creation link, he must provide information (organization name, initial domain name and country/region).
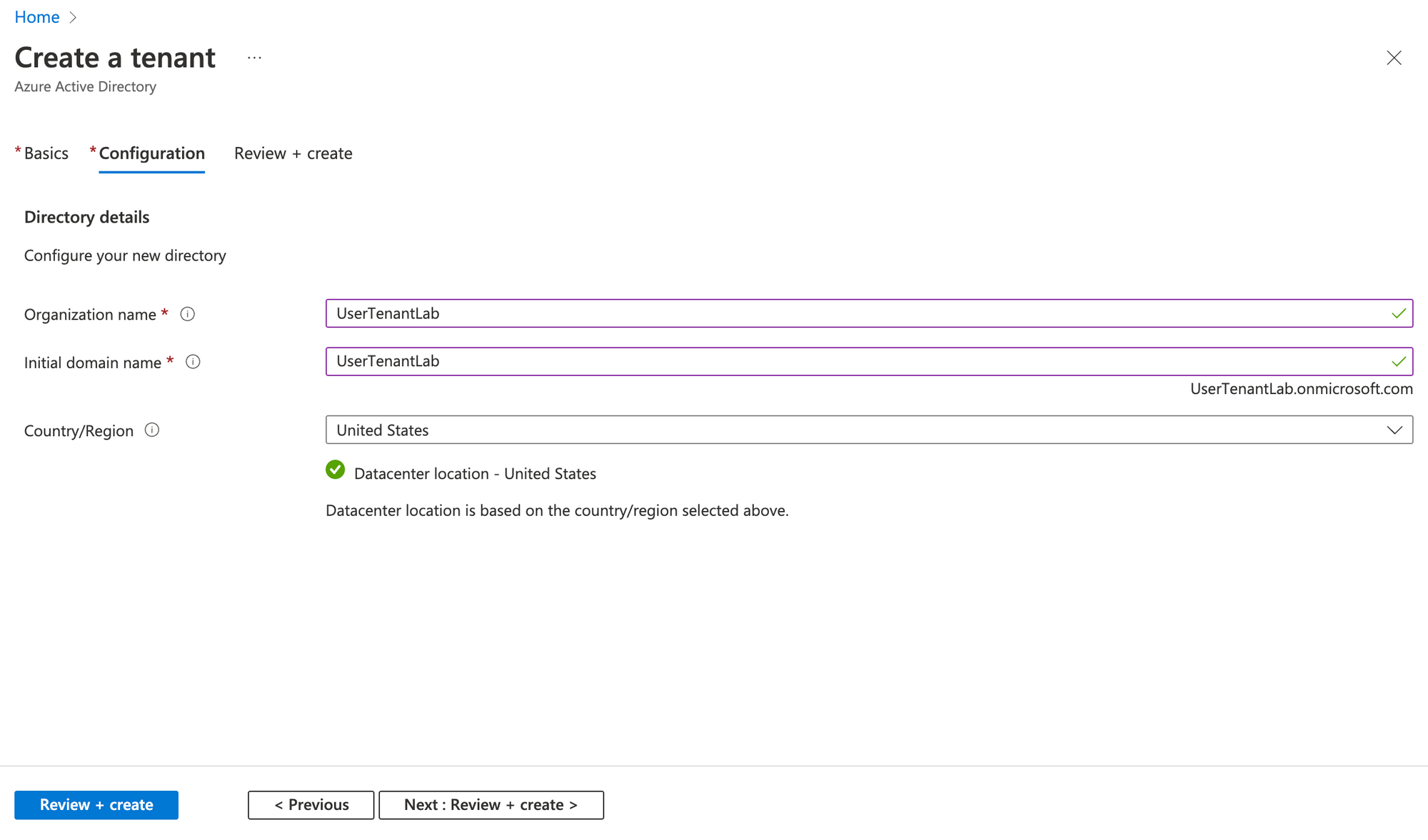
After waiting few minutes, the tenant is created. The user can switch between the corporate tenant and his own tenant:
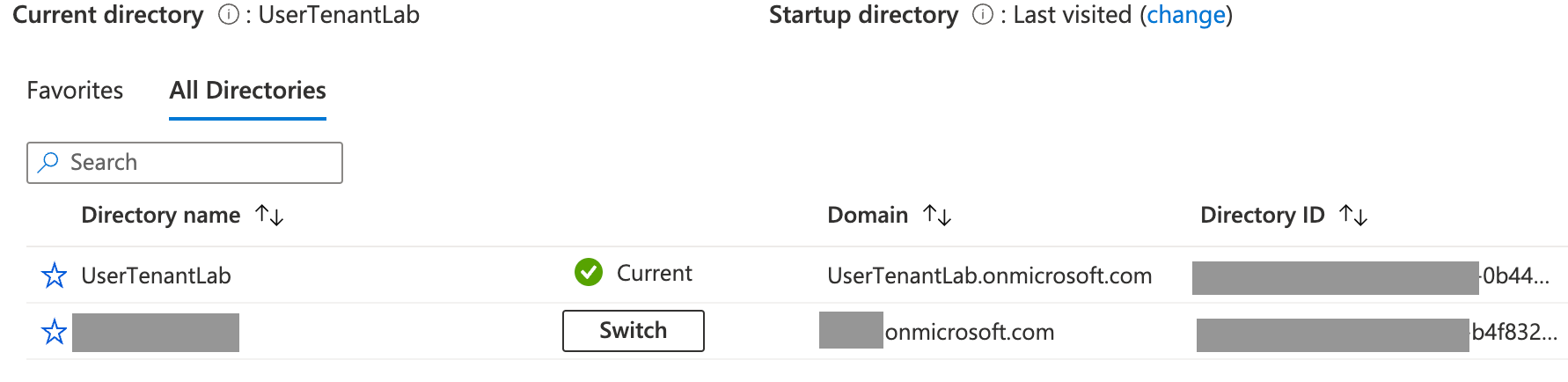
A thing to know is the user is a member of the tenant but with an ExternalAzureAD identity.
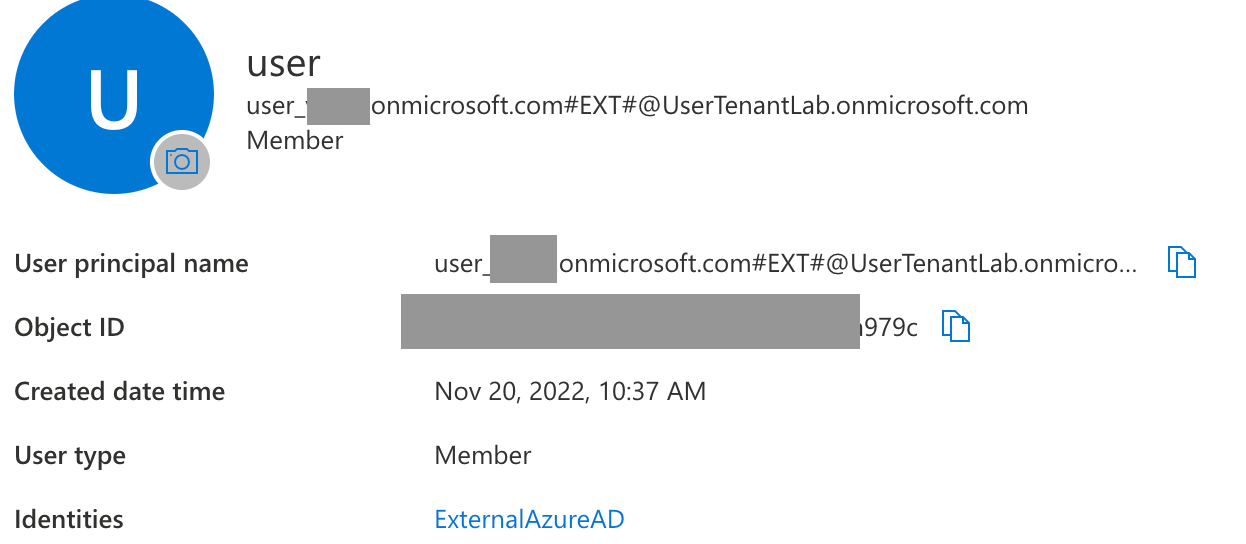
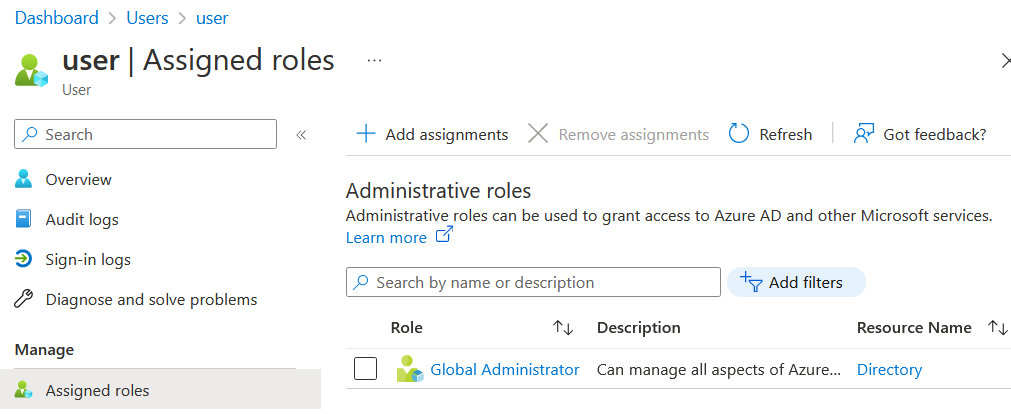
The user is global admin of his own tenant:
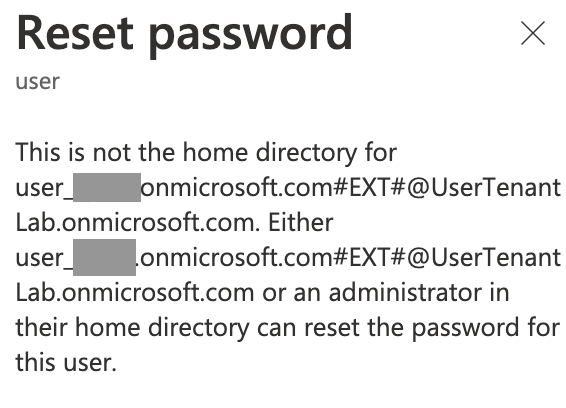
Because of this, the user can't reset/change his password into his own tenant for this account.
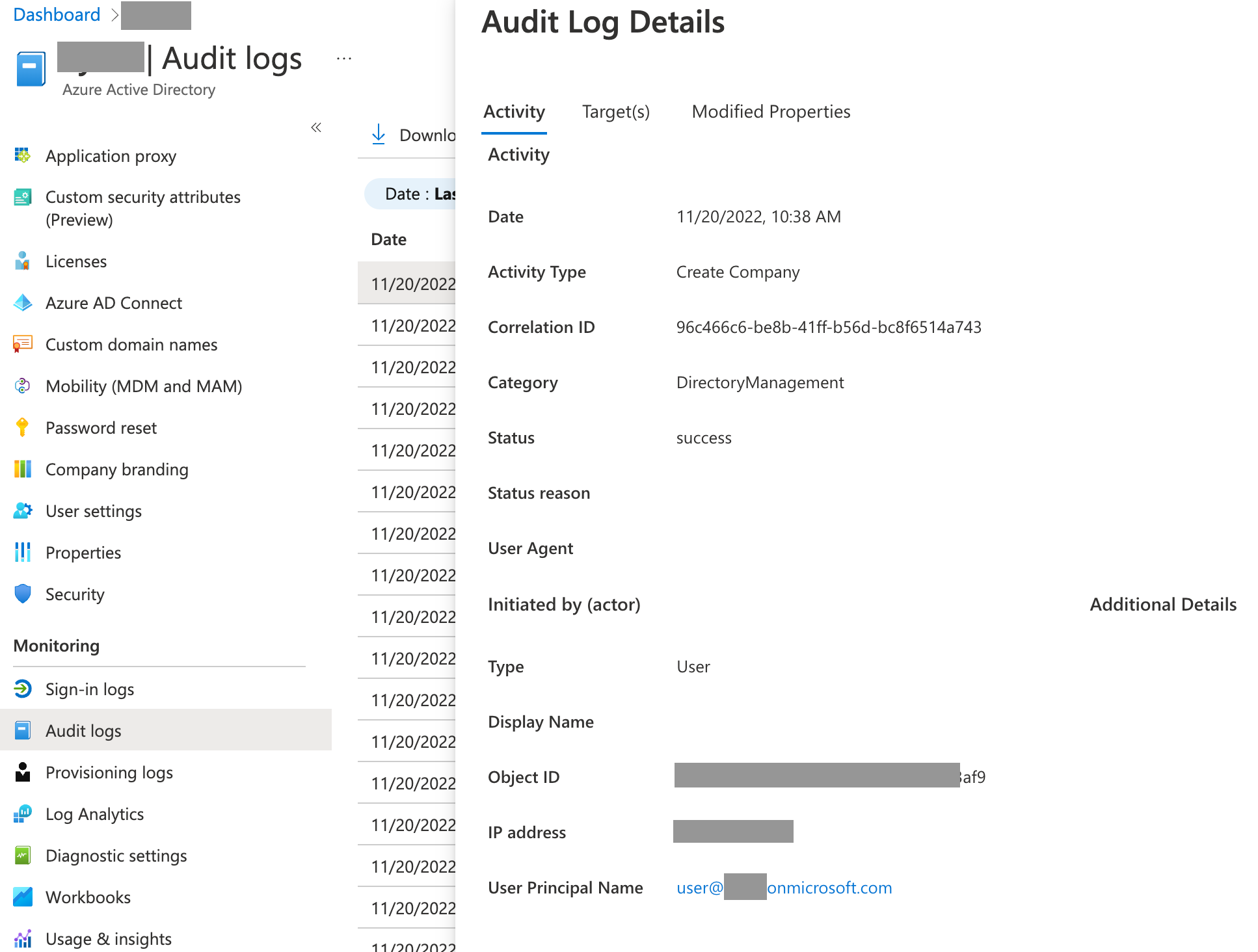
In the corporate tenant, admin can view the action in the Audit Logs with Activity Type Create Company. Of course, admin of the corporate tenant does not get any info about this tenant (at least, in GUI, not tried with Graph API) and is not able to switch to the newly tenant created by the user.
Once the Azure AD tenant creation is disabled, user can't create any new Azure AD tenant and get 403 error code.
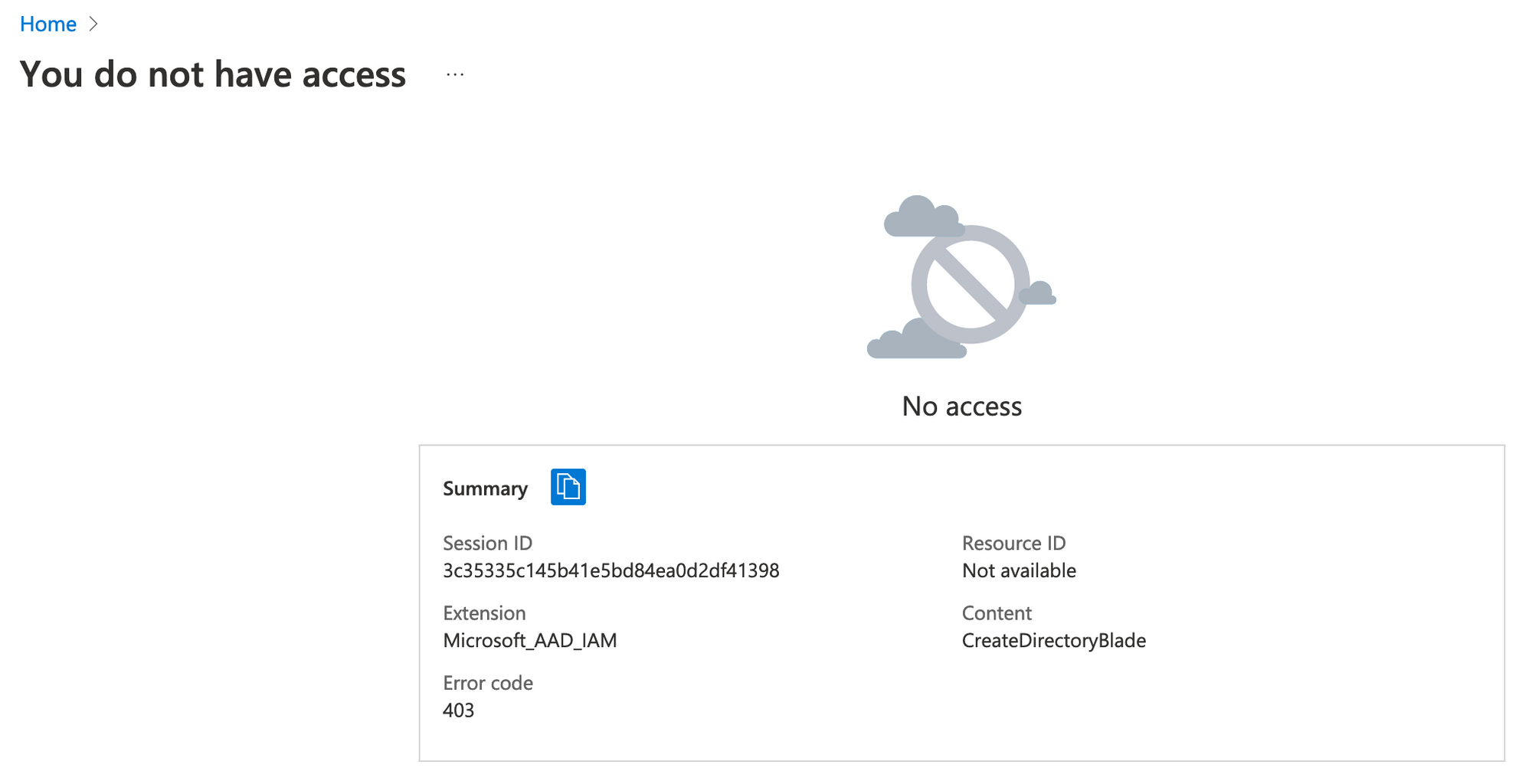
Impact of deletion user account in corporate tenant
As the user used the corporate identity to connect to his own tenant, the user can't connect to his own tenant.
Disable Azure AD tenant creation
It can be a best practice to disable this setting.
This sections show you how to disable AD tenant creation, either via web portal, or PowerShell or Microsoft Graph API.
The feature gives tenant administrators the ability to lock down tenant creation by their users and restrict it to only users with Global administrator or Tenant Creator role. For information about the Tenant Creator role, see the end of the article.
Disable with portal
Go to https://aad.portal.azure.com/#view/Microsoft_AAD_IAM/ActiveDirectoryMenuBlade/~/UserSettings (or, if you want to use Entra: https://entra.microsoft.com/#view/Microsoft_AAD_UsersAndTenants/UserManagementMenuBlade/~/UserSettings/menuId/UserSettings)
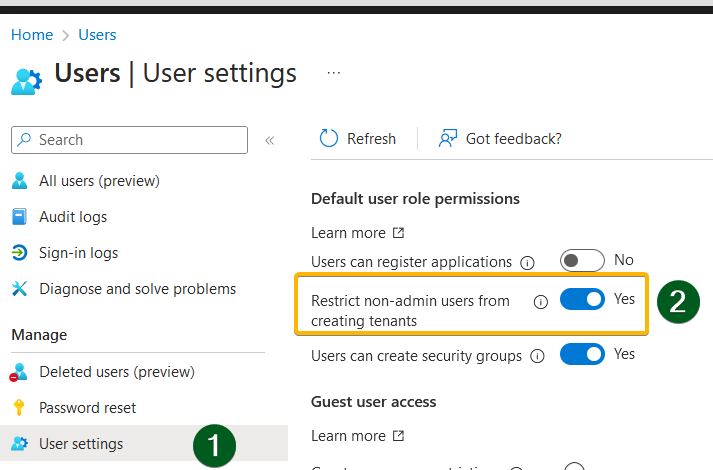
Since the beginning of 2023, the setting is now 'Restrict non-admin users from creating tenants.' Before, it was called 'Users can create Azure AD tenants.' I suppose Microsoft renamed this feature to provide a better understanding.
- Restrict non-admin users from creating tenants : No
Disable with PowerShell
Policy.ReadWrite.Authorization is needed.
# Load module. Make sure to have the last version
Import-Module Microsoft.Graph.Identity.SignIns
# Connect to Microsoft Graph with required scope
Connect-MgGraph -Scopes 'Policy.ReadWrite.Authorization'
# Update default authorization policy
Update-MgPolicyAuthorizationPolicy -DefaultUserRolePermissions @{AllowedToCreateTenants = $false}Disable with Microsoft Graph API
Policy.ReadWrite.Authorization is needed.
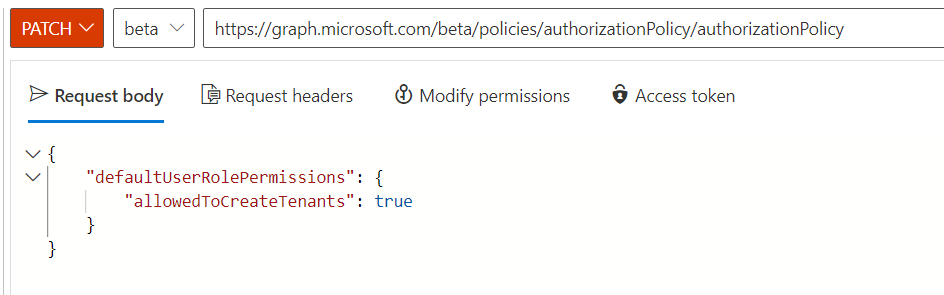
PATCH https://graph.microsoft.com/beta/policies/authorizationPolicy/authorizationPolicy
The body is:
{
"defaultUserRolePermissions": {
"allowedToCreateTenants": true
}
}In Microsoft Graph Explorer, it looks like this:
You can find logs about this in Audit logs:
Allow specific users to create tenants
If you need to allow specific users to create tenants (with 'Restrict non-admin users from creating tenants' set to 'Yes'), you can assign them the Tenant Creator role (https://entra.microsoft.com/#view/Microsoft_AAD_IAM/AllRolesBlade).
Clap



Comments